You may have heard about the large Ransomware attacks in the UK on Friday and Saturday – 12th May 2017.
You need to read below…. but in Summary.
Your email account / company IS being attacked by Ransomware every day.
Question is – Are you protected?
At the very least…. you need to
- Train or explain to colleagues to NOT open emails that you are not expecting.
- Consider deleting emails that you, or they, are not expecting
- Install latest AV Software, preferably via a managed system, on ALL PCs/Server
- Review AV reports and web traffic into your system to review protection.
- Train or explain to colleagues to not go on spurious websites from work PCs.
- Ensure ALL IT equipment has latest OS security updates – this can only be done via an RMM system.
- Ensure your Firewall is running latest software / systems.
Even with this protection you are still not guaranteed of being virus free.
So, next you need a plan of what to do if, or when, you are infected.
- Do you have Secure Back-ups that HAVE been tested?
- Back-ups without testing are almost worthless.
- What files are included in these back-ups. Consider what files are NOT included – Your PC?
- How long will it take you to restore these files?
Finally, although not recommended, you may need to consider paying the Ransom which will be approx. €500 per PC.
If you want help with any of the above…please contact us.
We supply RMM to protect companies against Ransomware and other security risks.
We test backups and restore data to existing or new/remote hardware.
In the meantime, please review the below and consider how will your company react if infected.
You need to plan for the inevitable infection.
Best Regards
Enda Downey
00353 21 4544144
*********************************************
Current Ransomware Issues
As you’re probably aware, on Friday, the NHS in the U.K., and many other companies, Nissan, Fedex etc were crippled by the latest ransomware virus – known as Wanna Decryptor 2.0.
As of now, it does not appear to have hit Ireland too much – but this is purely only a matter of time.
How does it spread?
It’s early days yet, but per most Malware Ransomware specialists, this virus appears to spread by phishing emails. One common email is to do with a bank requesting information on a money transfer. (Though there are other similar spoof emails carrying the virus.) These emails are usually associated with Brand names that we are familiar with and hence…. can easily open same. The difference with this virus though, is that once it’s opened on ANY machine on your network, it will try to move across other machines – and generally succeeds – thereby spreading the infection throughout your network.
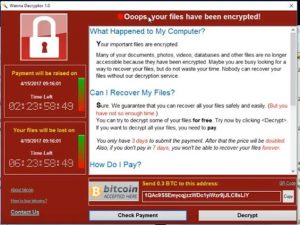
If I get it?
If you get infected, you’ll see a screen similar to:
At this stage, you have several options.
- You can pay the ransom (currently slightly less than €500). We strongly advise against this option. Firstly, it encourages the virus creators – and, you’re paying the money with no traceability! You’ve no guarantees that you will get your files back.
- You can try to restore your files from a backup. A couple of issues with this are:
- This virus will attempt to also encrypt your backup files – so depending on your solution this may not be an option.
- Generally, (though not always) a fileserver will be backed up, but a user’s workstation will not be – so you’ll have no formal backup of your workstation files. (i.e. files on your desktop, in your My Documents etc).
- You MAY be lucky. Sometimes a virus will not operate the way it was written to, and we may be able to retrieve some or all your files from system restores, shadow explorer files etc. – but this is NOT normally the case. You are very lucky if this succeeds for you.
- You can just write off your loss – and not retrieve your files. Normally this is not an option for obvious reasons. If you decided to do this, you can keep a copy of the encrypted files in the hopes that in the future, somebody will come up with a means of decrypting them. With previous versions of ransomware, this has sometimes happened – but there are no guarantees of this!
What have we in Compuland been doing?
We have had staff working all weekend on this.
- Our primary aim has been to ensure our RMM (managed) clients have everything up to date, windows patches, anti-virus etc.
- We’ve been keeping abreast of all the techie news coming out about the spread of the virus – trying to see any new options in repairing / stopping it.
- We’ve been keeping a weather eye on the main AV products and how they appear to be performing. Independent sites say that the two best products currently performing against this attack are BitDefender & Kaspersky. BitDefender has been our anti-virus of choice for some time now. We’ve been offering it as a stand-alone managed AV solution, and it’s also integrated into our Maxfocus/Solarwinds Remote Monitored Managed System. As these virus’s change format and methods of infection rapidly, it would be naive to suggest that any one AV product will always protect, but BitDefender seems excellent at adapting with the attack. Apart from looking for the specific virus files, it also monitors processes and stops any process that looks to be doing “virus like” behaviour – thus blocking viruses that it doesn’t even know about. A fair achievement!!
It’s very difficult to get a fully “independent” review of anti-virus products. You can find pretty much a site saying any AV solution is “the best”!! But looking around, I found a review by the Gartner Group – who would really have to be independent.
https://www.gartner.com/reviews/market/endpoint-protection-platforms/vendor/bitdefender/ratings
It’s interesting reading! BitDefender gets 4.5 out of 5 stars overall, and 4.9 out of 5 for Product Capabilities!! Can’t get much better than that!
What should you do?
OF HUGE IMPORTANCE – STRESS TO YOUR COLLEAGUES NOW, NOT TO OPEN AN EMAIL THAT THEY DON’T RECOGNIZE!! While this is always best practice, it is particularly important now when there’s such an epidemic out there!
Ensure that all machines are updated fully. Keeping all windows updates etc. up to date, helps block a lot of the vulnerabilities that can allow these viruses to run.
- Ensure your anti-virus is up to date and running. If you’re not using our Remote Managed Service, or our managed anti-virus – we’d strongly recommend that you swap over to it now!
- What form of backup do you use? A very good tip is if it’s to a USB drive, or USB key, do NOT leave the key or drive plugged into the machine. If it’s plugged in and you get infected, the virus will try to infect the key or drive too.
- Re your system backup, have you tested it recently? We’ll be glad to arrange a full restore test for you. At a minimum, we’d suggest you should restore a good number of your key files – just to prove it’s working at all – but we’d strongly recommend a “full” restore. Why wait until you’ve lost everything before you know any issues that might occur? Invest in a test system recovery now and see where you WOULD be if issues were to occur.
Finally, can I say that as ever, our job is to make your life easier from an IT perspective!
We will help in any way we can.
Bets to Plan for the infection….and hope it does not happen!!.